SIM CARD ATTACKS 2020 MUST READ
⭕🖤⭕🇰🇦🇱🇮™⭕🖤⭕METHODS OF SIM CARD HACKS
First: SIMJacker Attack
Due to your increasing personal and financial information tied to your online identity, attacks and hackings of phone numbers are more likely to occur. According to AdaptiveMobile Security, which is a company specialized in mobile phone security, the attack takes place through a defect and a gap in the SIM cards called (SIMJaker). This is capable of opening a back door for the hackers to attack the SIM card, and short SMS is enough to do the mission.
How Does It Happen?
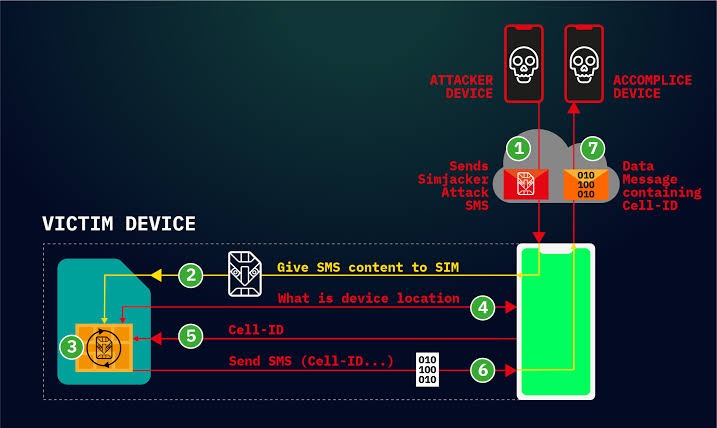
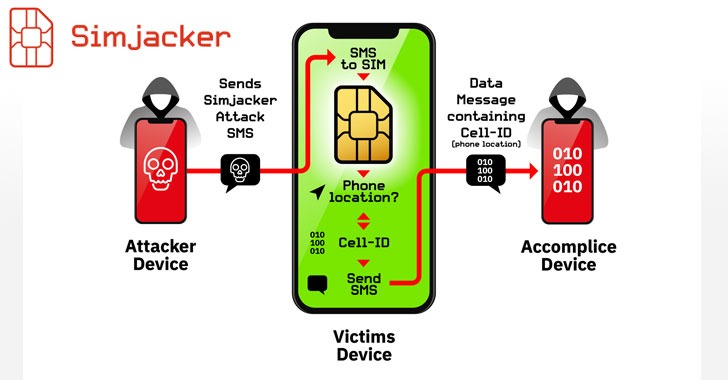
SIMJacker attack starts with an attacker sending an SMS to your smartphone. This SMS contains a link to a browser or a specific code commanding the SIM to disclose some data or to help control the device using a piece of software called S@T Browser, which is part of the SIM Application Toolkit (STK) that many phone operators use on their SIM cards. It is worth mentioning that such a process happens silently, not noticeable to you. Also, the SIMJacker hack is not limited to a specific operating system, and all types of phones are at risk, including smartphones that run on Android and iPhone.
The information pulled out from your SIM card contains your cell-ID which can determine your location and some specific device information like the IMEI from the handset. After that, the attack sends the data to a device other than the one from which the attacker sends the SMS in the hacking process. Then the attacker will be able to spy on your phone calls, steal your credits or hijack your bank accounts when linking your email to your phone number.
Second: SIM Swap Attacks
Hackers did compromise the personal account of Jack Dorsey, CEO and co-founder of Twitter. The penetration of Jack’s phone number linked to the account allowed the hackers to post a hail of offensive tweets for 15 minutes.
How Did the Hack Happen?
This hack is called “SIM Splitting or SIM Swap” in which the hackers take over your phone number and, as a result, all of your linked accounts. That is,
- The attacker deceives your service provider and impersonates you in order to ask for their technical support to issue a new and alternative SIM card.
- They can steal your phone number and link it to their own devices.
- Once the process is completed, the provider will cancel and suspend your real SIM card.
- The hacker will be able to access your phone calls and messages, bank accounts, e-mail and much more.
Let’s rethink the vast amount of sensitive information associated with your Google account:
- Address, birthdate and other personal information.
- The photos that may harm you personally.
- Calendar and upcoming travel dates.
- Emails, documents and search history.
- Personal contacts and their private information.
- All other online services that have used your primary email address as a source of authentication.
Third: SIM Cloning
It is worth noting that each SIM card is equipped with three basic codes:
- The International Mobile Subscriber Identity Code (IMSI) identifies the SIM data in international networks. This code consists of the country code or the network ID that you use.
- The (ICCID) code is the serial number of the SIM you are using. It is not the serial number of the mobile phone but the chip. Each chip has its own serial number.
- (Ki) code is the main code that the hacker needs. It identifies the card in the network and also protects it. If the hacker decodes the (Ki) code, he will be able to tweak your chip and own it.
By obtaining this data, cloning will be possible. As for the IMSI and ICCID codes, a SIM card reader can identify them, while it cannot read the other code (Ki) in the same way. However, hackers can use other clever methods to scan the (Ki). Consequently, the chip is copied to a writable, programmable card that telecom companies don’t supply, but hackers sell it online. There are several online programs and applications that attackers can download to decode these codes and copy your SIM data after reading it and work to write it on a new chip that can be written and programmed.
Victims may feel that something is suspicious. As a result, they may inform the telecom company to locate the geographical penetrator of the attacker. However, you should take care not to leave your SIM out of your sight because the cloning process requires the hacker to obtain your tangible SIM card or can use other ticks.

4.) WIB ATTACK
As an alternative to static SIM toolkit applications with a fixed pre-installed menu, some operators opt for dynamic SIM toolkit, where the menus and user dialogs are generated on the fly based on information provided by a central server. SIM applications that provide this functionality are generally referred to as SIM-browsers or µ-browsers.
Two browsers are currently available, the Wireless Internet Browser (WIB) which was the first successful browser released and promoted on the market by SmartTrust.
The Wireless Internet Browser (WIB) is specified by SmartTrust and is the market leading solution for SIM toolkit based browsing. The WIB-enabled SIM has a menu stored on the SIM. This menu can be managed and updated using Over The Air (OTA) services.
Attack Scenario
Attack Scenario is summarized in figure.

(1) Attacker sends a malicious OTA SMS to the victim phone number. The OTA SMS contains WIB command such as: SETUP CALL, SEND SMS, PROVIDE LOCATION INFO, etc.
(2) Right after receiving the OTA SMS, Baseband Operating System of the victim mobile phone uses ENVELOP COMMAND ( an APDU command to communicate between mobile phone and simcard) to forward the TPDU of the OTA SMS to WIB browser in victim’s simcard.
Different from the procedure of receiving the normal text sms, the procedure OTA SMS is silently handled just in baseband operating system and does not raise any alert to application operating system (android os, ios, blackberry os, …). Neither feature phone nor smart phone raises alert about the procedure of ota sms: no ringing, no vibration, no detection from users.
WIB browser follows the WIB commands inside the TPDU of OTA SMS and sends the corresponding PROACTIVE COMMAND to the victim mobile phone such as: SETUP CALL, SEND SMS, PROVIDE LOCATION INFO.
(4) The victim mobile phone follows the PROACTIVE COMMAND received from victim’s simcard to perform the corresponding actions such as: make a phone call, send an sms to whatever phone number attacker wants (e.g receiver mobile phone in the figure).
For attack scenario of getting victim’ location, it contains 2 phases in a single malicious OTA SMS. First phase, the ota sms instructs the WIB browser send PROACTIVE COMMAND ( PROVIDE LOCATION INFO) to the victim mobile phone. Second phase, instructs the WIB browser to send a PROACTIVE COMMAND (SEND SMS) with sms payload containing the response from the victim mobile phone (Cell ID, Lac ID). Attacker can use many websites on internet to convert the Cell ID, Lac ID to gps location on map.
WIB Commands
Several sensitive WIB commands which can send remotely via OTA SMS to victim’s sim card.

The SIM can issue a variety of commands through this mechanism, given in alphabetical order:
….
– DISPLAY TEXT, which displays text or an icon on screen. A high priority is available, to replace anything else on screen.
- LAUNCH BROWSER, which requests a browser inside a browser enabled ME to interpret the content corresponding to a URL.
– OPEN CHANNEL, which requests the ME to open a data channel with parameters indicated in the command (if class “e” is supported.)
– PLAY TONE, which requests the ME to play a tone in its earpiece, ringer, or other appropriate loudspeaker.
– PROVIDE LOCAL INFORMATION which requests the ME to pass local information to the SIM, for example the mobile country and network codes (MCC + MNC) of the network on which the user is registered.
– SEND SHORT MESSAGE, which sends a short message or SMS-COMMAND to the network.
– SEND SS, which sends an SS request to the network.
– SEND USSD, which sends a USSD string to the network.
– SET UP CALL, of which there are three types:
– set up a call, but only if not currently busy on another call;
– set up a call, putting all other calls (if any) on hold;
– set up a call, disconnecting all other calls (if any);
…..”” [4]
[4] 3GPP TS 11.14 V8.18.0 (2007-06)
3.4. Security mechanisms of OTA SMS
OTA (Over-The-Air) is a technology used to communicate with, download applications to, and manage a SIM card without being connected physically to the card.
OTA enables a Network Operator to introduce new SIM services or to modify the contents of SIM cards in a rapid and cost-effective way.
OTA is based on client/server architecture where at one end there is an operator back-end system (customer care, billing system, application server … ) and at the other end there is a SIM card.

The operator’s back-end system sends service requests to an OTA Gateway which transforms the requests into Short Messages and sends them onto a Short Message Service Centre (SMSC) which transmits them to one or several SIM cards in the field.
Thus, Over-The-Air (OTA) is a technology that updates and changes data in the SIM card without having to reissue it. Indeed, the end user can receive special messages from the operator, download or activate new services on his telephone, and much more …, without having to return to a retail outlet.
In order to implement OTA technology, the following components are needed:
- A back end system to send requests
- An OTA Gateway to process the requests in an understandable format to the SIM card
- An SMSC to send requests through the wireless network
- A bearer to transport the request: today it is the SMS bearer
- Mobile equipment to receive the request and transmit it to the SIM card
- A SIM card to receive and execute the request
However, OTA SMS can also be sent from peer to peer, i.e from mobile subscriber to mobile subscriber.
❤SO LETS TALK ABOUT HOW HACKER PERFORM ALL THESE ATTACKS 💙
💙CLONING A SIM CARD ❤
Step 1: Remove the SIM from the phone, place it in the card reader, click read from the card in magic SIM.
When it displays ‘connected’, select crack SIM in the toolbar.
Step 2: Click strong KI and select all of the other find options and then click start.
Once your KI is found and the crack is finished, click the file, save as and save your cracked SIM info to a file.
Step 3: You must click disconnect from the file menu or you will ruin your SIM card. [Important, Otherwise SIM will crack]
Step 4: Once it says disconnected. Remove the SIM. Put the SIM in your phone and see if it still works, it should.
(If not, either you did not unlock your SIM, or you tried to copy it instead of crack and save.)
Unlock SIM Card
Go to phone tools, select SIM card, then select unlock SIM, it will prompt for a code.
Call network provider, they will ask for your phone number, your account info, name, and security code, then they will ask why you want to unlock your SIM card, just tell them you need to unlock your SIM to get it to work with your overseas phone or something.
Once they give you the SIM unlock code, enter it, and it will say SIM unlocked.
Step 5: Insert blank SIM card and open USB SIM Card Reader Software not magic SIM at this point.
Step 6: Click connect. It should say ‘No Info Found’ if it is truly blank.
Step 7: Select write to SIM, it will prompt you to select a .dat file, select the one you saved earlier.
Step 8: Now click start, it will take about 10 minutes to write it, once it is complete, it will ask for a security code, enter the security code the network provider gave you, then click Finish. 👈
DONE: You have successfully cloned a SIM Card. 🔥
SIMCARD CLONING TOOLS :
http://mister-sim.software.informer.com/
https://www.dekart.com/products/card_management/sim_explorer/
https://www.amazon.com/Cellphone-Reader-Cloner-Writer-Backup/dp/B00ZWNGPX6/
https://ssl-download.cnet.com/MagicSIM/3000-2094_4-10601728.html
http://www.mobiledit.com/sim-cloning/
🙃🙃Here I am going to share a simple trick for block your enemy sim card,Blocking a sim card is too simple.🙃🙃
Dial the below code in the desired phone :- 04*3814*7529*68243#
Entering of above code will ask you to enter the PUK code.
To get PUK Code just call customer care and get your PUK code.
Note :- Entering of invalid PUK will cause permanent blocking of your SIM!
For Educational Purpose Only!
Try At Your Own Risk!
🖤ICCID explained🖤
An ICCID (Integrated Circuit Card Identifier) is a globally unique classifier that can be used to identify SIM hardware (most prominently physical SIM cards). This 19 to 20 character-long number is stored digitally, but typically also physically engraved into the SIM card's body. The ICCID may sound similar to an IMEI, but both are used to identify entirely different components. Physical eSIMs have an eUICCID, which is a different classifier; however, they are typically also assigned an ICCID.
What is the difference between an ICCID, IMSI, and IMEI?
The ICCID was conceived to identify all SIM hardware. However, there are other identifiers that are used for mobile network equipment. The most prominent ones are IMSI and IMEI:
IMSI
The IMSI (International Mobile Subscriber Identity) number is what cellular networks used to identify a specific subscription that is included as part of your data plan. Every time a device wants to establish a connection to the network, the network will identify the device by the IMSI. While this may sound similar to ICCID, both of these identifiers were conceived to identify different entities. The ICCID is used to identify the SIM Hardware, while the IMSI is used to identify the type of connectivity service.
IMEI
The IMEI (International Mobile Equipment Identity) number is typically printed on the batter component of any device with networking capabilities. It is a unique identifier for each device and is checked against a worldwide IMEI database when connected.
eSIMs and eUICCIDs
With the emergence of eSIMs (embedded subscriber identity module) a new identification number, known as the eUICCID number, has been established. A company may want to manufacture physical eSIMs but also generate and sell eSIM profiles. In some cases, these carriers will collaborate with other providers in order to create eSIM profiles, which means multiple parties may be involved in the creation of an eSIM. To simplify this situation and avoid confusion, the networking industry has created the eUICCID to identify physical eSIMs separately. The eUICCID number is an entirely different and unique classifier, however, an ICCID is typically still created along with the eSIM profile.
🖤🖤ICCID/SIM Card Number Checker/Decoder🖤🖤
To help you to obtain detailed information from the ICCID (Integrated Circuit Card Identifier) number, or SIM (Subscriber Identity Module) card number, FYIcenter.com has designed this online tool. All you need to do is to enter an ICCID/SIM Card Number in the form below, and click the "Decode" button. Detailed information of the ICCID/SIM Card Number will be presented in the result area.
http://phone.fyicenter.com/1155_ICCID_SIM_Card_Number_Checker_Decoder.html
👨💻👨💻👨💻NOW LETS COME TO OUR MAIN TOPIC👨💻👨💻.
HOW HACKERS HACK YOUR DATA .
USUALLY YOUR ALL DATA ARE SAVED IN MANY WEBSITES LIKE FLIPKART AMAZON ,DIGITAL LOCKERS ETC.
FIRST THEY COLLECT YOUR DATABASE FROM HACKING FORUMS
EITHER THEY EXTRACT THEIR OWN
DUMPS ( DATA ) FROM WEBSITE VIA
SQL INJECTION ....
OR THEY COLLECT YOUR DATA FROM SHOPS AND GENERAL STORE OR USUALLY BY PERFORMING PHISHING ATTACK ,COOKIE THEFT ETC !
THEN THEY STARTED DOXING !
MEANS THEY STALKING YOUR ALL ACTIVITIES AFTER GETTING MORE INFORMATION ABOUT VICTIM THEY
HACK THEIR ACCOUNTS AND AFTER GETTING CARD DETAILS THEY RIP YOUR MONEY ..............................
AFTER GETTING ICCID OF YOUR SIM CARD THEY FIND YOUR ALL DETAILS .
AND SPOOFED YOU !!!!!!!!!!!!!
🖤Popular Computer Forensics Tools🖤
Digital Forensics Framework
Digital Forensics Framework is another popular platform dedicated to digital forensics. The tool is open source and comes under GPL License. It can be used either by professionals or non-experts without any trouble. It can be used for digital chain of custody, to access the remote or local devices, forensics of Windows or Linux OS, recovery hidden of deleted files, quick search for files’ meta data, and various other things.
Download: https://github.com/arxsys/dff
The Sleuth Kit
The Sleuth Kit is a Unix and Windows based tool which helps in forensic analysis of computers. It comes with various tools which helps in digital forensics. These tools help in analyzing disk images, performing in-depth analysis of file systems, and various other things.
Volatility
Volatility is the memory forensics framework. It used for incident response and malware analysis. With this tool, you can extract information from running processes, network sockets, network connection, DLLs and registry hives. It also has support for extracting information from Windows crash dump files and hibernation files. This tool is available for free under GPL license.
Read more about the tool: http://code.google.com/p/volatility/
Computer Online Forensic Evidence Extractor (COFEE)
Computer Online Forensic Evidence Extractor or COFEE is a tool kit developed for computer forensic experts. This tool was developed by Microsoft to gather evidence from Windows systems. It can be installed on a USB pen drive or external hard disk. Just plug in the USB device in the target computer and it starts a live analysis. It comes with 150 different tools with a GUI based interface to command the tools. It is fast and can perform the whole analysis in as few as 20 minutes. To law enforcement agencies, Microsoft provides free technical support for the tool.
Official website: https://cofee.nw3c.org/
👨💻🖤LETS TALK ABOUT SAFETY TIPS🖤👨💻
How To Keep Your SIM Card Safe
If you want to protect your SIM card against attacks like these, there are some steps you can take.
Protect Against Socially Engineered Attacks
To protect against SIM card swaps, you should make it hard for hackers to find information about you. Hackers will use data they find about you online, such as names of friends and family or your address. This information will make it easier to convince a customer support agent that they are you.
Try to lock down this information by setting your Facebook profile to friends-only and limiting the public information you share on other sites. Also, remember to delete old accounts you no longer use to prevent them being the target of a hack.
❤Stay clear of sending sensitive data across public Wi-Fi networks
❤Use double verification systems
❤Do not share your passwords or leave them lying around
❤Keep an eye on your credit score
❤Watch out for phishing websites and fake campaigns
❤Use an antivirus program on desktop and mobile
❤Shop only at reputable websites
❤Keep data divulging on social networks to a minimum
❤Only download software from reputable sources
❤Be aware of social media-spread fake contests and links
❤Always use Familiar Websites
❤Avoid Public WiFi
❤Always check for the Lock (HTTPS) in Websites
❤Watch out for Phishing Scams
❤Keep up to date with Security Trends & Features
❤Consider using a Virtual Credit Card Number.
❤Always use 2 step verification.
👨💻REGARDS =@its_me_kali
#leechers copy with credit.
❤💙THIS POST IS JUST ONLY FOR EDUCATIONAL PURPOSE💙❤.
Комментарии
Отправить комментарий